For Corperations & Entities
What is a Cyber Threat Analysis & Sharing (C-TAS) System? Service Home
- KISA has established a Cyber Threat Analysis & Sharing (C-TAS) system to work with domestic and foreign companies and organizations to respond early to cyber threats and prevent the spread of damage due to the intelligence and advancement of cyber threats.
- The C-TAS system shares information on various cyber threats that occur widely across different industries among member companies.
- From January 2022, we opened an open website to expand participation of SMEs so that all companies that want threat information can receive threat information separately from the existing API service.
-
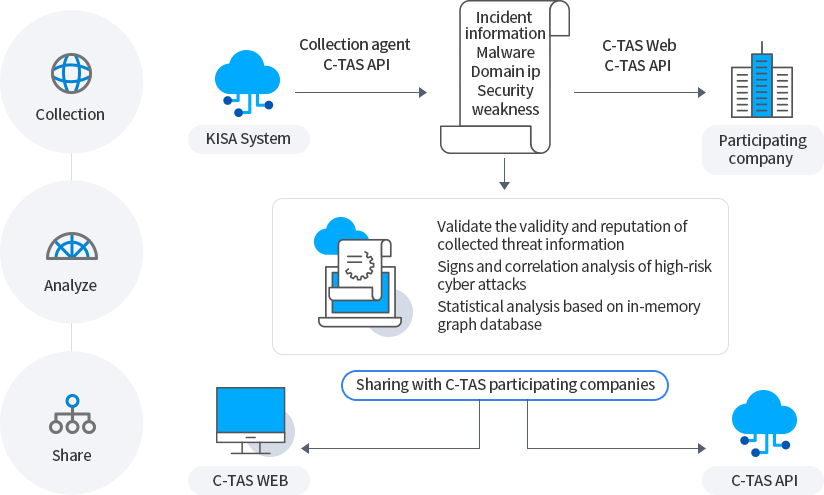
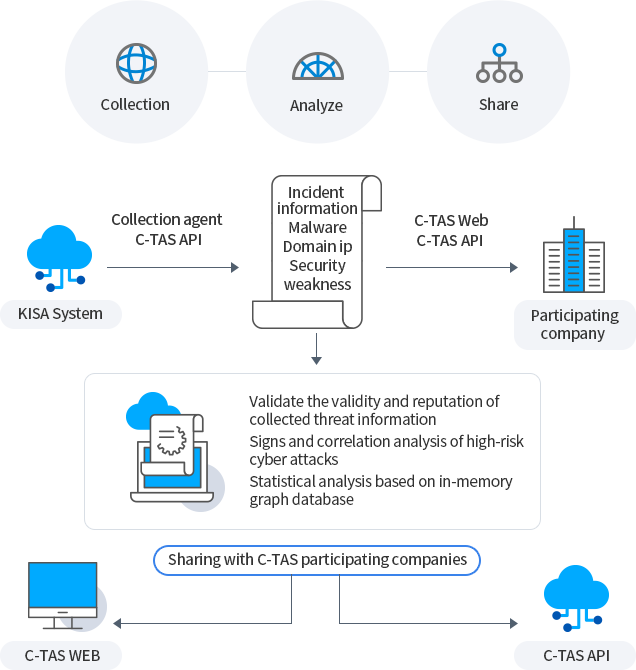
Collection
-
Analyze
-
Share
-
KISA System
Collection agent C-TAS API -
Incident information, Malware, Domain ip, Security weakness
C-TAS Web
C-TAS API -
Participating company
-
- Validate the validity and reputation of collected threat information
- Signs and correlation analysis of high-risk cyber attacks Statistical analysis based on in-memory graph database
-
C-TAS WEB
-
Sharing with C-TAS participating companies
-
C-TAS API
C-TAS WEB
-
- You can sign up for membership through the web page without a separate procedure, and you can use it after the administrator's sign-up approval.
- When signing up, the duties in charge are divided into [Supervisor / Employee], and information tailored to each responsibility is provided.
- Unlike API members, only threat information provided by KISA can be shared. We are implementing a real-time situation propagation system (information via text message (Kakao Talk) and e-mail in case of an emergency) service.
Usability
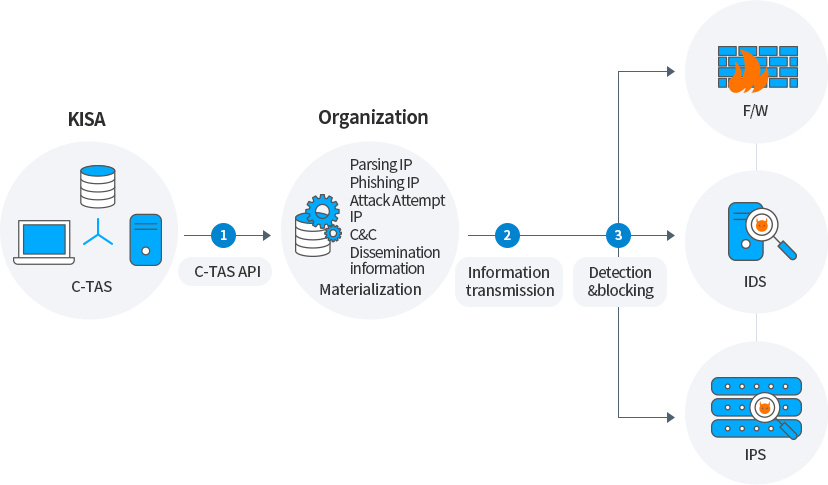
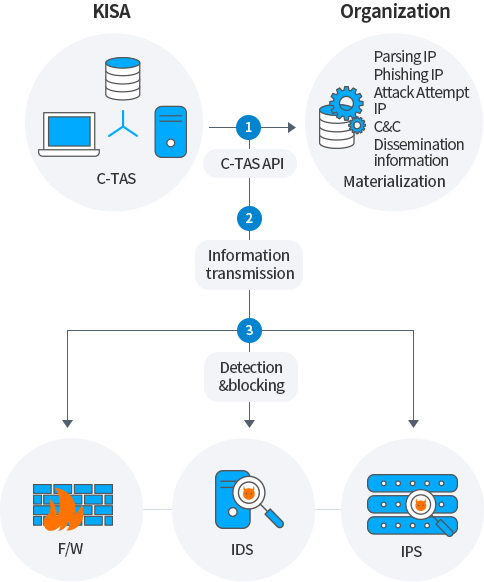
By utilizing information such as pharming IP, phishing IP, attack attempt IP, C&C, distribution site, etc., it can be stored in a DB (internal threat DB) and applied to security equipment such as in-house IPS, IDS, F/W, etc.
-
KISA
C-TAS
1C-TAS API
-
Organization
Parsing IP
Phishing IP
Attack Attempt IP
C&C
Dissemination informationMaterialization
2Information transmission
-
-
F/W
-
IDS
-
IPS
3Detection&blocking
-
You can utilize malicious code information to store it in a DB (internal threat DB), register the hash value of malicious code in the in-house anti-virus solution, and use it for diagnosing malicious code.
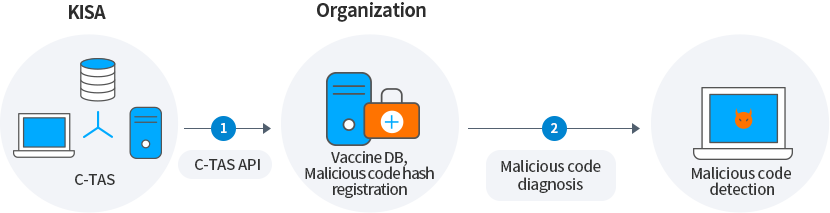
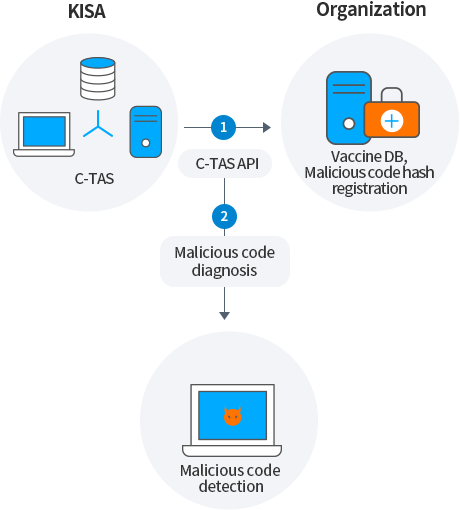
-
KISA
C-TAS
1C-TAS API
-
Organization
Vaccine DB, Malicious code hash registration
2Malicious code diagnosis
-
Malicious code detection
It can be used to compare hash values with files uploaded through web services, and to detect and block malicious files after storing them in a DB (internal threat DB) by utilizing malicious code and malicious e-mail information.
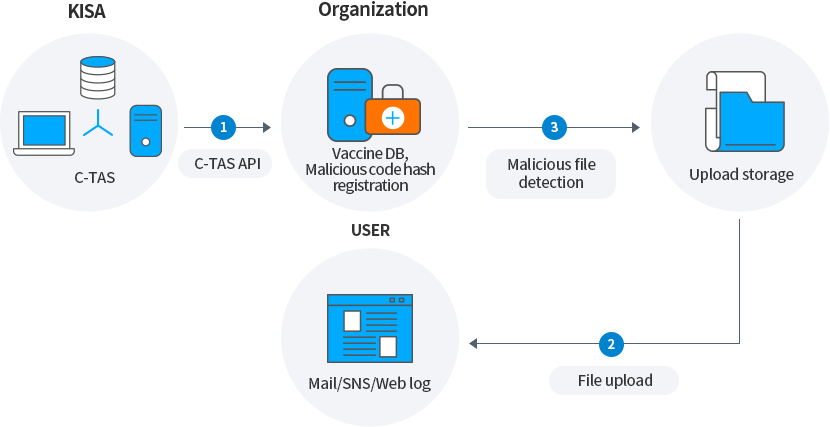
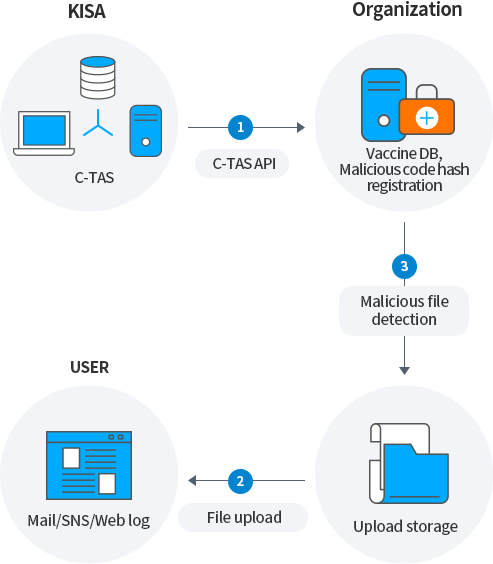
-
KISA
C-TAS
1C-TAS API
-
Organization
Vaccine DB, Malicious code hash registration
3Malicious file detection
-
Upload storage
-
USER
Mail/SNS/Web log
2File upload
Number of cyber threat prevention information sharing cases
| Division | 2017 | 2018 | 2019 | 2020 | 2021 | 2022 | 2023 |
|---|---|---|---|---|---|---|---|
| Prevention information sharing |
13,084,087 | 18,680,096 | 25,644,364 | 39,269,185 | 60,969,451 | 96,193,927 | 153,494,722 |